Air Force software platform expansion stalled by cybersecurity concerns

Efforts to expand the Air Force’s software development environment, Platform One, have stalled after some senior military IT leaders raised cybersecurity concerns about the platform, FedScoop has learned.
The concerns center on officials’ understanding of the architecture, policies of the environment and a perceived lack of security documentation. Some officials have tried to outright ban the use of code stored in one of its repositories, and reciprocity talks with other services have been held up over differences of the risk levels each is willing to take, multiple sources with knowledge of the matter told FedScoop.
Platform One’s success, and replication across the military, could have huge impacts for developers that need a secure method of coding to have their products cleared by DOD authorizing officials. But to achieve widespread use, officials across multiple services need to sign off on its use, and reciprocity with similar coding environments needs to be negotiated among the services.
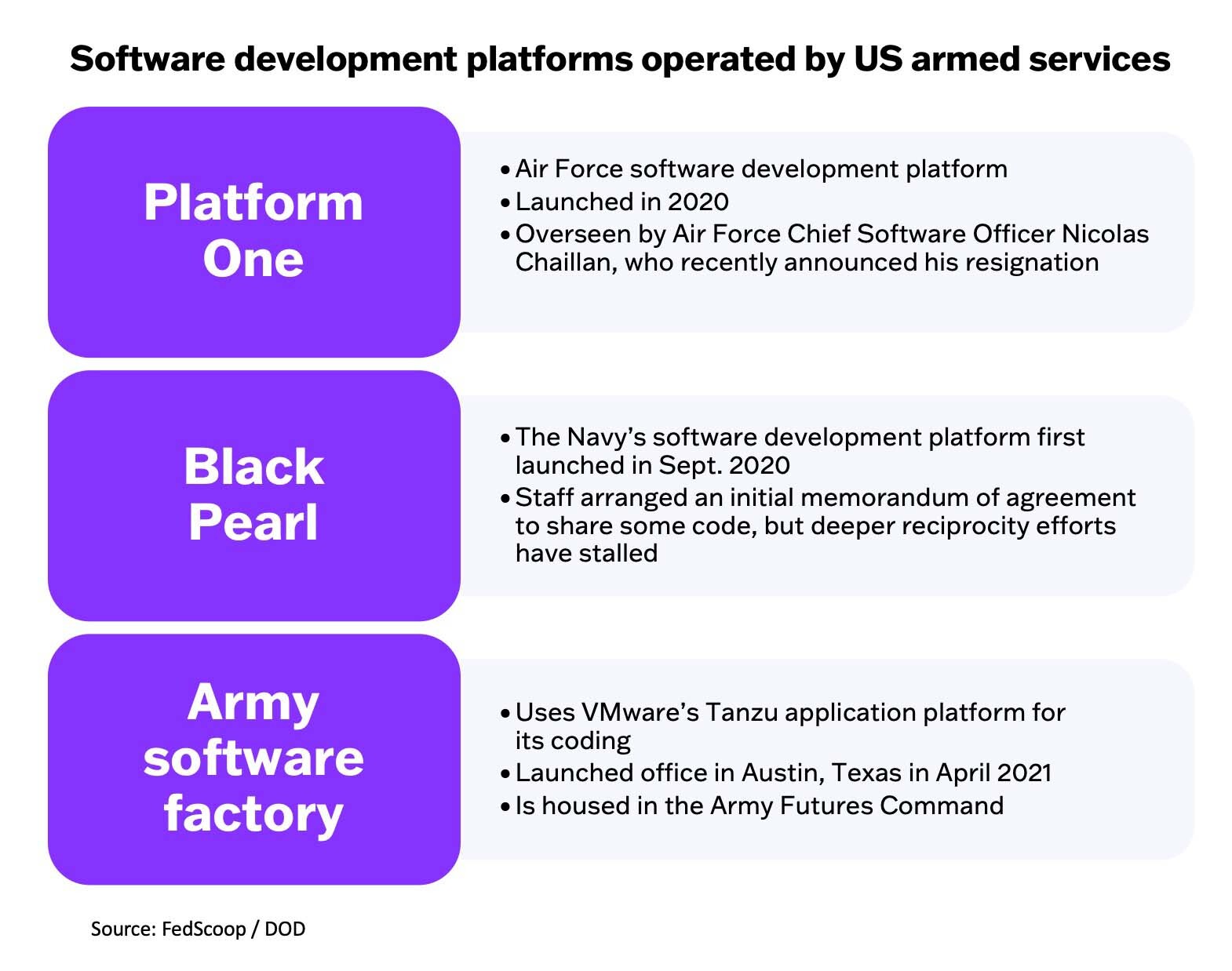
Platform One is one of the Air Force’s main offices for digital innovation. The service is focused on navigating around Department of Defense bureaucracy to build tech that it says is more secure than DOD’s current risk-averse processes. The office’s core tech runs on Google’s Kubernetes, an open-source system for securely storing code in containers. It has been touted by its leaders as a key enabler in the DOD’s push to make itself a digital organization by leveraging what’s called DevSecOps — a technical and cultural approach to writing code that integrates security at every level of development.
“As pioneers, all of these programs broke glass and were met by many with celebration and by some with hesitancy,” Lauren Knausenberger, the Air Force’s CIO, said in a statement provided to FedScoop. She added: “We’re doing our best to educate folks on new technologies and processes and use their experience to help continuously adapt.”
Instead of following the DOD’s de facto process for software authorization, Platform One was able to get its process cleared so that new code authorization is automated, essentially accrediting a recipe rather than testing each batch.
DOD’s process for software authorization forces developers to submit code to a months-long checklist-based approval process each time they want to make an update. Some IT officials say this can leave software systems vulnerable to breaches because they are forced to remain stagnant while updates are checked.
By focusing on the processes of writing code, advocates for Platform One say it is more secure, quicker and in line with commercial best practices.
“Platform One prioritizes cybersecurity over compliance checks. Do people want to be secure or do people want to be compliant? Both take work, and some prioritize one over the other,” Rob Slaughter, Platform One’s former director, told FedScoop.
But despite Platform One’s perceived improved security processes, officials that want to use it say they have concerns.
The problem for some, Slaughter said, is: “They [Platform One] just don’t have the homework in the right format.”
Speaking to FedScoop, former DOD CISO Jack Wilmer said the individual issues raised by officials were not outright dangerous on their own, but demonstrated that without a way for services to have a common understanding of mitigating cyber risk, it’s difficult to achieve reciprocity.
Several officials who have asked for Platform One’s security documentation said they were not provided with any, creating mistrust in the system. Officials who had discussed using Platform One or were familiar with its practices told FedScoop they felt the patching process was too ad-hoc for their comfort and authorization for new containers was too centralized.
Officials also had acute concerns around one of Platform One’s Iron Bank product, which stores open-source code in containers. The issues with Iron Bank center around a perceived lack of verification of who is contributing and a lack of a legal framework for issuing patches for code stored on the system.
Some of the concerns about the patching process and software supply chain for Iron Bank were brought to the attention of the DOD CIO’s office during a meeting about expanding the use of Iron Bank, according to two officials familiar with the meeting.
Emails reviewed by FedScoop indicate that officials have “a desire for more transparency and input into the vetting process” of containers in Iron Bank.
Danielle Metz, deputy CIO for information enterprise who chaired the meeting, said such meetings are regular occurrences to help develop Iron Bank’s tech.
“The implementation of software containers is a rapidly growing but still relatively nascent field for the DoD. The Air Force’s Iron Bank has been at the forefront of identifying secure and repeatable processes for software development and insertion into Platform One and other programs throughout the DoD,” she said in a statement to FedScoop.
Knausenberger heralded the role of Platform One in breaking new tech barriers in DOD and told FedScoop that many of the concerns come down to a misunderstanding of the new tech.
“These programs all do things differently,” she said.
The Navy is working on its own DevSecOps platform similar to Platform One called Black Pearl. Officials in the Navy and Air Force have been negotiating a reciprocity agreement to avoid the Navy re-doing work already accomplished by Platform One. But talks stalled over technical details concerning the way Platform One accepted risk and how it stored documentation about its security practices, officials said.
A Navy spokesperson told FedScoop in a statement that it is “strongly engaged” in platform collaboration and that it’s working to ensure the cybersecurity practices “are transparent and repeatable to maximize reciprocity.”
“The Department of the Navy and our partners are committed to seeing that work through,” the spokesperson said.
Navy officials had requested documentation through the Enterprise Mission Assurance Support Service (eMASS), an application that stores security packages. Since Platform One doesn’t follow the traditional compliance processes, it says its documentation is not in the format that is supported by eMASS. Instead the team “[automates] the vast majority of their security controls and checks, and store their real-time docs in their GIT repositories,” Knausenberger said.
“It still sometimes freaks out the security assessors because they are not used to finding real-time documents in a code repo,” she said.
Knausenberger added that Platform One sometimes attracts criticism because it regularly works with cybersecurity red teams — white hat hackers tasked with playing the role of the adversary — and. because the teams are good at what they do, they occasionally identify vulnerabilities.
“Each time they do, these teams take it very seriously, they learn from the findings, and they make fixes very quickly. Compare that to legacy programs that submitted a checklist at a point in time and may not know what issues are there now, or may not be able to fix them quickly. While change can make people uneasy this is the type of change we need to win,” Knausenberger said.





